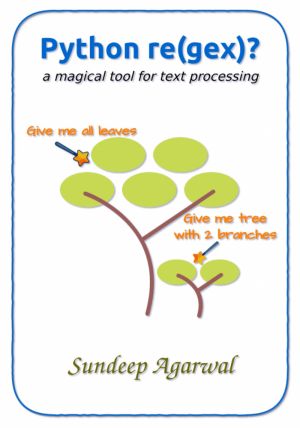
Scripting and automation tasks often need to extract particular portions of text from input data or modify them from one format to another.
This book will help you learn Python Regular Expressions, a mini-programming language for all sorts of text processing needs.
The book heavily leans on examples to present features of regular expressions ...
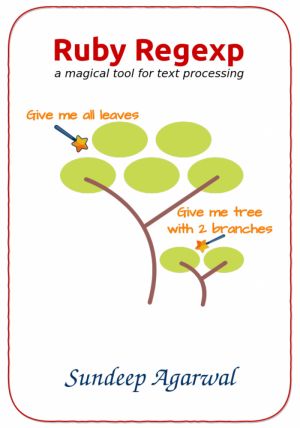
Scripting and automation tasks often need to extract particular portions of text from input data or modify them from one format to another.
This book will help you learn Ruby Regular Expressions, a mini-programming language for all sorts of text processing needs.
The book heavily leans on examples to present features of regular expressions on...

If you're looking to gain an introduction into the world of user experience (UX) design - or maybe even freshen up your knowledge of the field - then this UX design book is the ideal place to start.
You'll cover a wide range of topics over nine highly readable chapters, with each one acting as a mini crash course. By the end, you'...

If you want a basic understanding of computer vision's underlying theory and algorithms, this hands-on introduction is the ideal place to start. You'll learn techniques for object recognition, 3D reconstruction, stereo imaging, augmented reality, and other computer vision applications as you follow clear examples written in Python.
Pro...

A study of Internet blocking and filtering around the world: analyses by leading researchers and survey results that document filtering practices in dozens of countries.
Many countries around the world block or filter Internet content, denying access to information that they deem too sensitive for ordinary citizens - most often about politics, b...

Internet filtering, censorship of Web content, and online surveillance are increasing in scale, scope, and sophistication around the world, in democratic countries as well as in authoritarian states. The first generation of Internet controls consisted largely of building firewalls at key Internet gateways; China's famous "Great Firewall o...

Big Data collected by customer-facing organisations - such as smartphone logs, store loyalty card transactions, smart travel tickets, social media posts, or smart energy meter readings - account for most of the data collected about citizens today. As a result, they are transforming the practice of social science. Consumer Big Data are distinct from...

From IT projects that have trampled all over the guiding principles of successful development, to tips on training your manager to the required standard, each of Phil's tales is shot through with a wild seam of anarchic humour. And yet, in each case, the humor is just a sugar coating for a pill of sage advice, wrought from years of rough-and-t...

The purpose of this book is to shed light on the performance and personal competencies of information technology (IT) project managers in South Africa. Predictive models are built to determine what project managers consider the crucial competencies they should possess to deliver an IT project successfully. This investigation takes place in the cont...

This book presents a series of activities to teach the basics of computer networks. While you will not learn all aspects of computer networking, we hope that it will serve as a good starting point.
To network micro:bits, we use custom micro:bit radio to radio communication. When one hears the word radio, what comes to mind is the radio that blas...

Firefox, a free Web browser developed by the Mozilla Foundation, is used by an estimated 270 million people worldwide. To maintain and improve the Firefox browser, Mozilla depends not only on its team of professional programmers and managers but also on a network of volunteer technologists and enthusiasts - free/libre and open source software (FLOS...

The Internet Myth retraces and challenges the myth laying at the foundations of the network ideologies - the idea that networks, by themselves, are the main agents of social, economic, political and cultural change. By comparing and integrating different sources related to network histories, this book emphasizes how a dominant narrative has extensi...

Since the growth of social media, human communication has become much more visual. This book presents a scholarly analysis of the images people post on a regular basis to Facebook. By including hundreds of examples, readers can see for themselves the differences between postings from a village north of London, and those from a small town in Trinida...

How are users influenced by social media platforms when they generate content, and does this influence affect users' compliance with copyright laws?
These are pressing questions in today's internet age, and Regulating Content on Social Media answers them by analysing how the behaviours of social media users are regulated from a copyrig...

How the World Changed Social Media is the first book in Why We Post, a book series that investigates the findings of anthropologists who each spent 15 months living in communities across the world. This book offers a comparative analysis summarising the results of the research and explores the impact of social media on politics and gender, educatio...

What constitutes a healthy diet? Mainstream media and advertisers would like you to think that the answer to this question is complicated and controversial. But science, fortunately, tells us otherwise.
A Conversation about Healthy Eating brings together all the relevant science about healthy eating in one place, and it's exactly that - a c...

Join us in the quest for building games for Firefox OS, the new mobile operating system by Mozilla. Empowered by this books practical approach you will learn thru examples how to develop a full game from the beginning all the way to the distribution in the Firefox Markeplace....

Learn how easy and quick it is to develop applications for Firefox OS, the new mobile operating system by Mozilla. Empowered by this books practical approach you will learn thru examples how to develop apps from the beginning all the way to the distribution in the Firefox Markeplace....
The book is a set of tutorials and examples. It uses the Common Lisp language and some of the libraries we'll be using for the examples and tutorials include:
- The hunchentoot web server
- The Restas web framework
- The SEXML library for outputting XML and HTML
- Closure-template for HTML templating
- Postmodern for PostgreSQL access, an...

There's a lot of outdated information on the Web that leads new PHP users astray, propagating bad practices and insecure code. PHP: The Right Way is an easy-to-read, quick reference for PHP popular coding standards, links to authoritative tutorials around the Web and what the contributors consider to be best practices at the present time.
T...

If you've toyed with Linux and never really caught on to what's happening or have used a graphical interface without really touching the command line this book is for you.
The idea is to get you started on the process of using some of the commands available in Linux so that you: Feel comfortable running commands; You understand a littl...

The ideal reader for this book will be quantitatively literate and has a basic understanding of statistical concepts and R programming. The book gives a rigorous treatment of the elementary concepts in statistical inference from a classical frequentist perspective. After reading this book and performing the exercises, the student will understand th...

This book walks you through a patterns-based approach to building real-world cloud solutions. The patterns apply to the development process as well as to architecture and coding practices.
Developers who are curious about developing for the cloud, considering a move to the cloud, or are new to cloud development will find here a concise overview ...

Cloud applications have a unique set of characteristics. They run on commodity hardware, provide services to untrusted users, and deal with unpredictable workloads. These factors impose a range of problems that you, as a designer or developer, need to resolve. Your applications must be resilient so that they can recover from failures, secure to pro...

In today's world of pervasive Internet connectivity and rapidly evolving Web technology, online security is as critical as it is challenging. With the enhanced availability of information and services online and Web-based attacks and break-ins on the rise, security risks are at an all time high. Hacking Exposed Web Applications shows you, step...

The book teaches you how to write web applications in Go without using a framework. It is possible to write a webapp without using any framework in Go. Each new concept will be explained via a valid code example. The book is based of a todo list manager I wrote in Go, and at any point in time, you can check the source code of the todo list manager....

Additive manufacturing or 3D printing, manufacturing a product layer by layer, offers large design freedom and faster product development cycles, as well as low startup cost of production, on-demand production and local production. In principle, any product could be made by additive manufacturing. Even food and living organic cells can be printed. ...

With its novel XOR-based metric topology, Kademlia is the first peer-to-peer system to combine provable consistency and performance, latency-minimizing routing, and a symmetric, unidirectional topology. In The Kademlia Protocol Succinctly, author Marc Clifton leads readers through the positive aspects of Kademlia's decentralized specifications...

When running a web application or service, there are three crucial elements to keep tabs on: availability, performance, and usage. A wide variety of technologies are available to monitor these things, but one that stands apart is Application Insights, a developer tool available through the Microsoft Azure cloud platform. In Application Insights Suc...

Skype is essential to communication across industries of all types, and even in our personal lives. Knowing how to use SDKs that allow developers to interact with Skype as a platform has become a valuable tool. In Skype Bots Succinctly, author Ed Freitas gives readers an in-depth exploration of the features in the Microsoft Bot Framework for Skype....

Entity Framework is Microsoft's flagship Object/Relation Mapper, and the recommended way to access relational databases. Entity Framework Core is a complete rewrite from the "classic" Entity Framework, building on the new multiplatform .NET Core framework and adding the ability to connect to nonrelational data sources while keeping t...

Containers have revolutionized software development, allowing developers to bundle their applications with everything they need, from the operating system up, into a single package. Docker is one of the most popular platforms for containers, allowing them to be hosted on-premises or on the cloud, and to run on Linux, Windows, and Mac machines. With...
