
This is an optimization manual for advanced C++ programmers. This book are not for beginners.
Topics include:
- The choice of platform and operating system.
- Choice of compiler and framework.
- Finding performance bottlenecks.
- The efficiency of different C++ constructs.
- Multi-core systems.
- Parallelization with vector operations.
- CPU dispa...
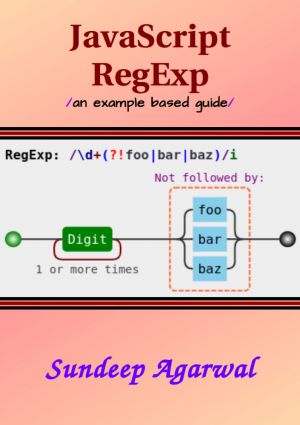
The book heavily leans on examples to present features of regular expressions one by one. It is recommended that you manually type each example and experiment with them.
You should have a good understanding of basic-level programming concepts and prior experience working with JavaScript. Should also know functional programming concepts like map ...

The book heavily leans on examples to present features of grep as well as regular expressions one by one. It is recommended that you manually type each example and experiment with them. Understanding both the nature of sample input string and the output produced is essential.
You should have prior experience working with command line and bash sh...
PicoLisp Works is a compilation of (almost) all available information about the technological gem PicoLisp - a programming language and environment that definitely deserves wider attention.
Built on the unique characteristics of Lisp (almost no syntax, code is equivalent to data), PicoLisp combines powerful abstractions with simplicity and purit...

In this practical guide to the law for young people of Canada, Ned Lecic and Marvin Zuker provide an all-encompassing manual meant to empower and educate children and youth and those that serve them. The authors address questions about how rights and laws affect the lives of young people at home, at school, at work, and in their relationships as th...

Written by members of the development team that maintains Subversion, this is the official guide and reference manual for the popular open source revision control technology. The new edition covers Subversion 1.7 with a complete introduction and guided tour of its capabilities, along with best practice recommendations.
Version Control with Subve...

PHP is a widely-used open source programming language. It is especially suited for web development. The unique thing about PHP is that it serves both beginners as well as experienced developers. It has a low barrier to entry so it is easy to get started with, and at the same time, it provides advanced features offered in other programming languages...

Vim is a console-based multi-mode (modal) text editor. It is widely used and available by default on all Unix, Linux, and Apple OS X systems. Vim has a large active community and a wide user base. The editor supports all popular programming languages, and many plugins are available to extend its features.
It is an unofficial and free Vim book cr...

LaTeX is a markup language for typesetting documents similar to how HTML is one for web sites. LaTeX is especially popular in academic writing due to its rich support for typesetting equations, cross-referencing figures and tables, and citations and bibliographies.
It is an unofficial and free LaTeX book created for educational purposes. All the...

This open book, like Rayleigh's classic Theory of Sound, focuses on experiments and on approximation techniques rather than mathematical rigor. The second edition has benefited from comments and corrections provided by many acousticians, in particular those who have used the first edition in undergraduate and graduate courses. For example, pha...

The emergence of the Internet of Things (IoT), combined with greater heterogeneity not only online in cloud computing architectures but across the cloud-to-edge continuum, is introducing new challenges for managing applications and infrastructure across this continuum. The scale and complexity is simply so complex that it is no longer realistic for...

Express is a Node.js Web Framework. Node.js is an amazing tool for building networking services and applications. Express builds on top of its features to provide easy to use functionality that satisfy the needs of the Web Server use case.
The Express Handbook follows the 80/20 rule: learn in 20% of the time the 80% of a topic. The author find t...

This book looks at some of the central issues in the philosophy of computer science. It is not designed to answer all (or even any) of the philosophical questions that can be raised about the nature of computing, computers, and computer science. Rather, it is designed to "bring you up to speed" on a conversation about these issues - to gi...

Defend Dissent is an introduction to cryptography paired with the social impacts of surveillance and the protective potential of encryption, with a focus on US social movements. Each chapter ends with a story that brings social context to the material - from surveillance used against contemporary US protests to the African National Congress's ...

This guide aims to aid people interested in learning to work with BASH. It aspires to teach good practice techniques for using BASH, and writing simple scripts.
This guide is targeted at beginning users. It assumes no advanced knowledge - just the ability to login to a Unix-like system and open a command-line (terminal) interface. It will help i...

Bash is the shell, or command language interpreter, for thegnuoperating system. Thename is an acronym for the 'Bourne-Again SHell', a pun on Stephen Bourne, the authorof the direct ancestor of the current Unix shellsh, which appeared in the Seventh Edition Bell Labs Research version of Unix.
Bash is largely compatible withshand incorpo...

As technology has developed, computer hackers have become increasingly sophisticated, mastering the ability to hack into even the most impenetrable systems. The best way to secure a system is to understand the tools hackers use and know how to circumvent them. Defense against the Black Arts: How Hackers Do What They Do and How to Protect against It...

Digital accessibility skills are in high demand, as the world becomes more aware of barriers in digital content that prevent some people from participating in a digital society. These are essential skills for web developers, and essential knowledge for organizations that want to ensure their web content is reaching the broadest audience possible.
...

The GNU Debugger allows you to see what is going on "inside" a program while it executes - or what a program was doing at the moment it crashed. GDB supports C, C++, Java, Fortran and Assembly among other languages; it is also designed to work closely with the GNU Compiler Collection (GCC). The GNU Debugger Program has four special featur...

This is an intro to C for folks who already know how to program in another language. The first half of the book is written in a tutorial style, while the second half is a reference section complete with examples (inspired by the incomparable Turbo C Bible). The goal is to keep this up-to-date with the latest C standards.
This guide assumes that ...

Back in the mid 90s, Beej got tired of all his friends asking him how to do this stuff with networking programming in C, so he put pen to paper on the early World Wide Web and wrote down everything he knew just to get them off his back. Since then, the Guide has expanded significantly, with plenty of examples, and covers IPv6. Inside you'll fi...

Linux crash analysis - this is a subject that has lots of unanswered mail threads and plain text documents scattered all over the place, inaccessible to almost everyone, save the tiny percentage of super geeks.
My personal and professional interest in the last three years has taken me down the path of Linux kernel secrets, all the way into assem...

When you start building your first containerized application, you're excited about the capabilities and opportunities you encounter: it runs the same in dev and in prod, it's straightforward to put together a container image using Docker, and the distribution is taken care of by a container registry.
So, you're satisfied with how ...

DevOps engineers, developers, and security engineers have ever-changing roles to play in today's cloud native world. In order to build secure and resilient applications, you have to be equipped with security knowledge. Enter security as code.
In this book, authors BK Sarthak Das and Virginia Chu demonstrate how to use this methodology to se...
